Templates
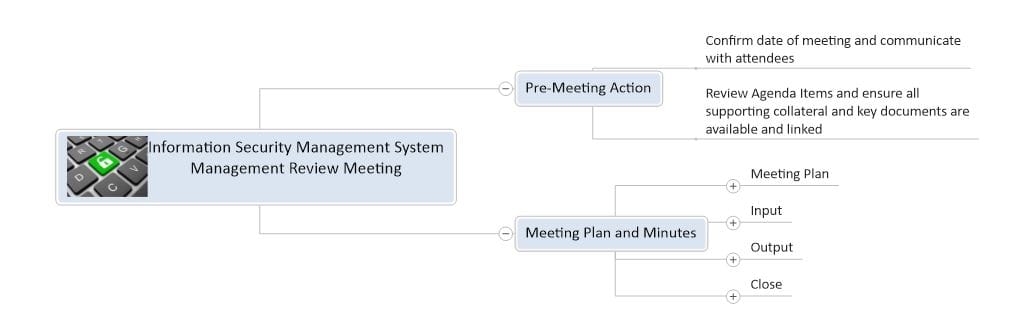
Information Security Management System Management Review Meeting Mind Map
Map out your problem using this template.
Don’t have MindGenius installed? No problem, simply start your free trial today to be able to download and open.
1. Pre-Meeting Action
1.1. Confirm date of meeting and communicate with attendees
1.2. Review Agenda Items and ensure all supporting collateral and key documents are available and linked
2. Meeting Plan and Minutes
2.1. Meeting Plan
2.1.1. Introduction
2.1.1.1. Date
2.1.1.2. Attendees
2.1.1.3. Apologies
2.1.1.4. Objective of the meeting
2.1.1.4.1. To ensure the continuing suitability, adequacy and effectiveness of the ISMS
2.1.2. Review Input
2.1.2.1. The status of actions from previous Management Reviews
2.1.2.1.1. Actions from meeting of (insert date)
2.1.2.2. Changes in external and internal issues that are relevant to the ISMS
2.1.2.2.1. Regulatory or legal requirements
2.1.2.2.2. Contractual obligations
2.1.2.2.3. People
2.1.2.2.4. Customers
2.1.2.2.5. Industry
2.1.2.2.6. Suppliers
2.1.2.2.7. Others
2.1.2.3. Feedback on the information security performance, including trends in:
2.1.2.3.1. Nonconformities and corrective actions
2.1.2.3.2. Monitoring and measurement results
2.1.2.3.3. Audit results
2.1.2.3.4. Fulfilment of information security objectives
2.1.2.3.4.1. Review information security strategy, plans, roles and responsibilities
2.1.2.3.4.2. Information security resourcing including budget and return on security investments
2.1.2.4. Feedback from interested parties
2.1.2.4.1. Directors
2.1.2.4.2. Staff
2.1.2.4.3. Customers
2.1.2.4.4. Others
2.1.2.5. Results of risk assessment and status of risk treatment plan
2.1.2.6. Opportunities for continual improvement
2.1.2.6.1. Implemented
2.1.2.6.2. In Progress
2.1.2.6.3. Planned
2.1.2.6.4. Suggested
2.1.2.7. Review Output
2.1.2.7.1. Decisions related to continual improvement opportunities
2.1.2.7.2. Any need for changes to the ISMS
2.2. Input
2.2.1. The status of actions from previous Management Reviews
2.2.1.1. Actions from meeting of (insert date)
2.2.2. Changes in external and internal issues that are relevant to the ISMS
2.2.2.1. Regulatory or legal requirements
2.2.2.2. Contractual obligations
2.2.2.3. People
2.2.2.4. Customers
2.2.2.5. Industry
2.2.2.6. Suppliers
2.2.2.7. Others
2.2.3. Feedback on the information security performance, including trends in:
2.2.3.1. Nonconformities and corrective actions
2.2.3.1.1. Dates (insert ‘From’ and ‘To’ dates).
2.2.3.1.2. Information Security Reports (ISRs) raised
2.2.3.1.3. Current Status of ISRs
2.2.3.1.3.1. Open
2.2.3.1.3.2. In Progress
2.2.3.2. Main reasons for ISRs being raised
2.2.3.3. Monitoring and measurement results
2.2.3.4. Audit results
2.2.3.4.1. Period (insert ‘From’ and ‘To’ dates)
2.2.3.4.2. Comments
2.2.3.4.3. Internal
2.2.3.4.3.1. Audits Performed During the Period
2.2.3.4.3.1.1. Number
2.2.3.4.3.1.2. Closed
2.2.3.4.3.1.3. Report Completed
2.2.3.4.3.2. Audit Findings
2.2.3.4.3.2.1. Audit Nonconformities
2.2.3.4.3.2.2. Observations
2.2.3.4.3.3. Current Status of Audit Findings
2.2.3.4.3.3.1. Audit Nonconformities Open
2.2.3.4.3.3.2. Observations Open
2.2.3.4.3.4. Audit plan in place for next (insert period) months
2.2.3.4.4. External
2.2.3.4.4.1. ISO 27001:2013 Surveillance Audit performed – (insert date)
2.2.3.4.4.2. Audit Findings Raised
2.2.3.4.4.2.1. Audit Nonconformities
2.2.3.4.4.2.2. Observations
2.2.3.4.4.3. Current status of Audit Findings
2.2.3.4.4.3.1. Audit Nonconformities Open
2.2.3.4.4.3.2. Observations Open
2.2.3.4.4.4. Next re-certification audit provisionally scheduled for (insert date)
2.2.3.5. Fulfilment of information security objectives
2.2.3.5.1. Review information security strategy, plans, roles and responsibilities
2.2.3.5.2. Information security resourcing including budget and return on security investments
2.2.4. Feedback from interested parties
2.2.4.1. Directors
2.2.4.2. Staff
2.2.4.3. Customers
2.2.4.4. Others
2.2.5. Results of risk assessments and status of risk treatment plan
2.2.5.1. Significant information risks (threats, vulnerabilities and impacts) and opportunities, including information security incidents affecting this or other organisations
2.2.5.2. Prioritisation of information risks relative to other business risks (risk register)
2.2.5.3. Risk treatments including information security projects and initiatives
2.2.6. Opportunities for continual improvement
2.2.6.1. Techniques, products or procedures that could be used in the business to improve the ISMS performance and effectiveness
2.2.6.1.1. Implemented
2.2.6.1.2. In Progress
2.2.6.1.3. Planned
2.2.6.1.4. Suggested
2.3. Output
2.3.1. Decisions related to continual improvement opportunities
2.3.2. Any need for changes to the ISMS
2.3.2.1. Improvement to how the effectiveness of controls is being measured
2.3.2.2. Resource needs
2.3.2.3. Modification of procedures and controls that affect information security
2.3.2.3.1. Changes to business requirements
2.3.2.3.2. Changes to security requirements
2.3.2.3.3. Changes to business processes affecting the existing business requirements
2.3.2.3.4. Changes to regulatory or legal requirements
2.3.2.3.5. Changes to contractual obligations
2.3.2.3.6. Changes to levels of risk and/or criteria for accepting risks
2.3.2.4. Update of the risk assessment and risk treatment plan
2.3.2.5. Confirm ISMS Scope and Objectives
2.4. Close
2.4.1. Actions
2.4.1.1. Recommendations for improvement
2.4.2. Next Management Review date
2.4.3. Any Other Business
